
Have you ever wondered where all the fuss about ransomware comes from? Surely you’ve heard about it at work or read about it in the news. Or maybe you’re just now getting a pop-up window on your computer warning you of an infection?
What is ransomware?
Ransomware is a malicious software that blocks users from accessing their systems or personal files and then demands a fee in exchange for its restoration. The first variants of ransomware were developed in the late 1980s and used traditional mail to send the ransom. Today, ransomware creators demand ransoms in the form of cryptocurrencies or credit card transfers.
How do you get ransomware?
There are various methods by which ransomware infects computers. One of the most popular is the sending of malicious spam (called malspam), i.e. unsolicited emails designed to spread malware. Such emails may contain infected files (e.g. PDF or Word documents) or links to malicious websites.
Malspam uses social engineering methods to encourage recipients to open attachments or click on links that are seemingly non-threatening, i.e. they appear to come from friends or trusted institutions. Cybercriminals also use social engineering for other types of attacks, e.g. posing as police officers to intimidate their victims and force them to pay fees to unblock files.
Malvertising is another popular infection method, with malicious advertising (malvertising) being at its most popular in 2016. Using this technique allows criminals to spread software via online advertisements, which in many cases requires very little (or no) participation from the potential victim. When browsing the web – even trusted sites – users can be redirected to criminals’ servers even without clicking on ads. These servers collect detailed information about the victims’ computers and their locations, and then select the best-fit malware to carry out the attack. In many cases, this is ransomware.

Types of ransomware
There are three main types of ransomware, varying in the severity of the threat:
Scareware
Scareware, or intimidation software, contrary to its name, is not all that scary. It usually works by impersonating security software or technical support staff. Scareware can, for example, display a pop-up window with information about a malware infection that requires a fee to remove. If we do not act, the software will probably continue to bombard us with pop-up windows, but our files should be safe.
It is worth remembering that developers of genuine security software will never acquire new customers in this way. What’s more, if we don’t have the company’s solution on our computer, it certainly won’t monitor it for infections. If, on the other hand, we do have such a product, we do not need to pay extra for malware removal – after all, we have already purchased it for this purpose.
Screen locks
This takes the threat to the next level! An infection from screen-blocking software completely prevents you from using your computer. When it is triggered, a full-screen message is displayed, usually containing a police or state security badge, information about the detection of illegal activity on the computer and – of course – a ransom demand. It is worth remembering, however, that none of these institutions block computers in this way or demand fees for illegal activity. If there is a genuine suspicion of the distribution of illegal software, child pornography or other illegal digital material, any contact is made through the appropriate legal channels.
Encryption software
Let’s move on to the most serious threats. It is this type of software that steals and encrypts files, demanding a ransom in return for unlocking and sending them back. The problem is serious because the encryption software hands over the infected files to the criminals, so no security software can help decrypt them. In most cases, non-payment of the fee entails the irretrievable loss of data. Unfortunately, even if we pay the ransom, we have no guarantee that the cybercriminals will return our data.
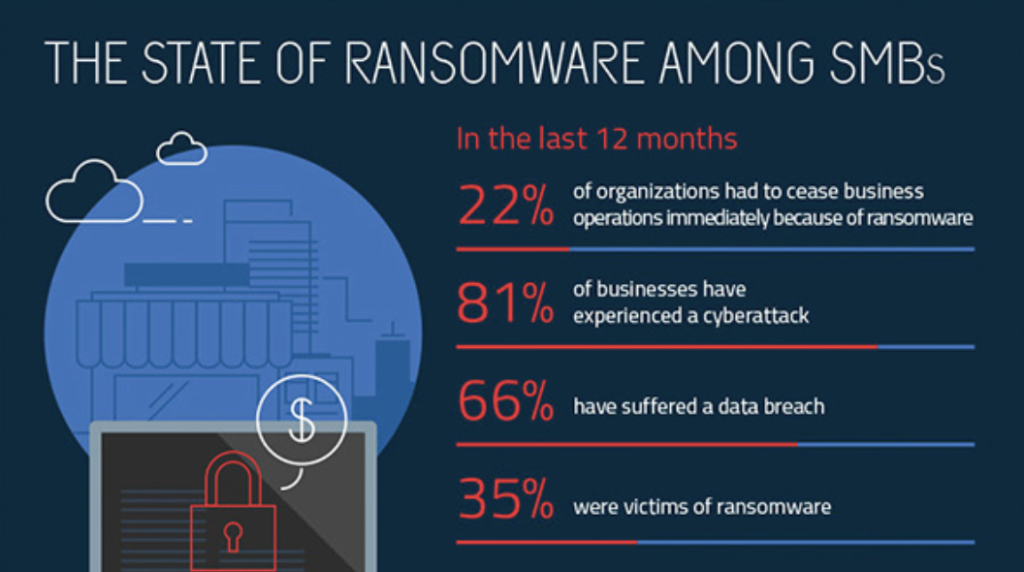
How do you protect yourself from ransomware?
Security experts agree: the best way to protect against ransomware attacks is to prevent them in the first place.
